# Webhook Security
# Overview
When data is exchanged over the internet, there is a risk of interception and modification, known as a man-in-the-middle attack. To protect against this, AppSumo includes security measures in every webhook sent to partners.
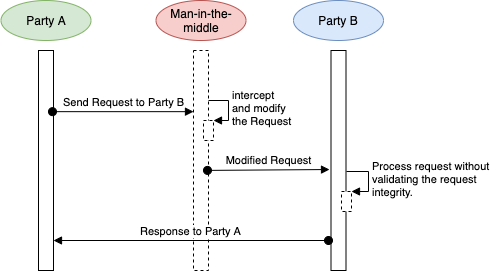
# Message Authenticity
Each webhook from AppSumo contains two security headers that help validate the integrity of the message, ensuring it has not been altered.
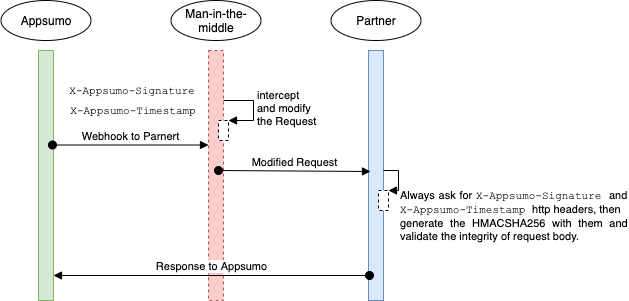
# HMAC SHA256
AppSumo uses the HMAC SHA256 algorithm, which creates a secure, one-way encryption to verify that the received data is exactly as sent.
- How It Works:
- AppSumo and the partner share an API Key used for both encryption and API requests.
- AppSumo creates a message by combining a timestamp with the request body and encrypts it using the shared API Key (See API: Getting started)
- This encrypted message (SHA) is sent to the partner in the HTTP header
X-Appsumo-Signature. - The timestamp is sent in the HTTP header
X-Appsumo-Timestamp, and the data is sent in unencrypted JSON format in the request body.
- Validation Process:
- The partner receives the timestamp and data, combines them to form a single message, and encrypts it using the API Key.
- The partner then compares the generated SHA with the value in
X-Appsumo-Signature. - If they match, the request is confirmed as authentic and unmodified.
# Verifying webhook requests (Optional)
The following codes are example of how an AppSumo Partner can generate the SHA with the data sent by AppSumo and compare both SHA message.
1